When preparing a Windows Server 2012 DirectAccess server with two network interfaces, proper configuration of the network interfaces is vital to the operation and security of the remote access solution, especially in edge-facing scenarios. Preparing a server with two network interfaces might seem trivial, but there are some important and often overlooked settings that may lead to trouble. In this post I’d like to outline the proper network interface configuration for a Windows Server 2012 DirectAccess server in an edge-facing deployment scenario. It is important to note that you should configure your network interfaces prior to installing and configuring DirectAccess.
The first step is to rename the network interfaces with intuitive names that identify their role. Typically I use Internal and External. This will make DirectAccess configuration much easier, as you will see when you are configuring DirectAccess using the deployment wizards. To rename the network interfaces, open the Networking and Sharing Center from the Control Panel and choose the option to Change adapter settings. Optionally you can simply highlight the network interface you wish to rename and hit F2. Assign new names to the network interfaces as appropriate.

Next, right-click the Internal network interface and choose Properties. Enter an IPv4 address, subnet mask, and DNS servers as required. Notice that I have not entered a default gateway here. This is absolutely critical and one of the most common mistakes made when configuring a multihomed DirectAccess server. On a server with multilple network interfaces there can be only one default gateway, and the gateway must reside on the External network interface.

In the absence of a default gateway on the Internal network interface, static routes will be required to reach any remote internal subnets. To add a static route, open an elevated PowerShell command prompt and add any necessary routes using the following syntax:
New-NetRoute -InterfaceAlias <Interface_Name> -DestinationPrefix <SubnetID/Mask> -NextHop <Gateway_Address>
For example, my lab network has a remote subnet of 172.16.2.0/24 that is reachable through a router interface of 172.16.1.254.
New-NetRoute -InterfaceAlias Internal -DestinationPrefix 172.16.2.0/24 -NextHop 172.16.1.254
It’s also a good idea to unbind any protocols that are not required. For example, in my implementation I will not be leveraging QoS or NIC teaming, nor will I require the Link-Layer Topology Discovery services so I’ve unchecked those boxes accordingly.

Perform this same exercise for the External network interface. Enter an IPv4 address and subnet mask, and this time be sure to include the default gateway for the External network. Notice that I have not entered any DNS servers here. Resist the urge to enter the DNS servers provided by your ISP. They are not required here.

Since this DirectAccess server will be edge-facing and connected directly to the public Internet, it is a good idea to unbind all protocols from the network interface with the exception of IPv4 and IPv6.

In addition, uncheck the option to Enable LMHOSTS lookup and also chooseDisable NetBIOS over TCP/IP.

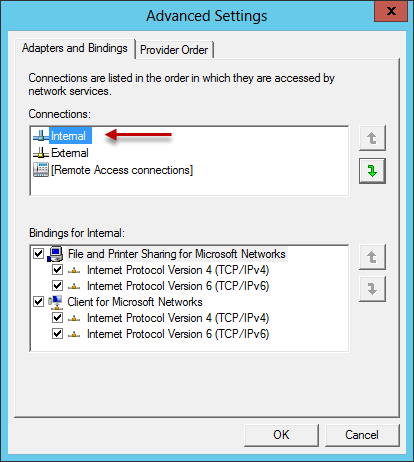
One last change that needs to be made, and perhaps the most critical and often overlooked setting, is the network interface binding order. This change can be made by pressing the Alt key on the keyboard to display the drop-down menu and choosing Advanced Settings.
Important Note: Beginning with Windows Server 2016, making changes to the network interface binding order is no longer required, and this option has been removed from the UI.

Make certain that the Internal network interface is listed first in the list of connections.
So that’s it! You can now proceed with installing and configuring DirectAccess in full confidence that your network interfaces are configured properly!
Additional Resources
Always On VPN and the Future of DirectAccess
5 Things DirectAccess Administrators Should Know about Always On VPN








waingro
/ June 20, 2013Good blog – are there any security considerations when standing up DA 2012 as an edge deployment? I want to think that it is hardened enough as is, but I need to actually know it and not just think it. Any links would be great. Thanks!
Richard Hicks
/ June 20, 2013Excellent question, and there are many. Coincidentally, that is the subject of a future post so stay tuned. 🙂
Richard Hicks
/ August 8, 2013Hi Jason,
PowerShell is the wave of the future! Time go stop using those legacy commands and learn the new, modern way for configuring Windows. 😉 Seriously though, I understand why many continue to use “route add”. If it works, no need to fix it, right? 🙂 I’ll update the post soon with some commands and screen captures using route add soon.
Thanks!
Mark
/ May 1, 2025In my environment have had to use route add for every new 2 NIC VPN deployment I have been using on Server 2022 for the internal NIC.
The command is:
route add 172.16.123.0 mask 255.255.255.0 172.16.123.1 -p
Do this for each of your VLAN routs on the LAN side then everything else on this blog clicks into place. Also you do not need to configure routes in the RRAS config as this supersedes them (and they don’t work anyways)
mike0788
/ September 10, 2013Excellent post. thanks Richard!
dnelre
/ September 30, 2013Hey Richard, it would be nice if you updated the post with the routing pictures 🙂
Richard Hicks
/ October 1, 2013If I can find the time, I will certainly do that. 🙂
NEUR0
/ January 22, 2015I know this is an old post but maybe you will see this. How do I add routes so that the DA server still has internet access? Also, the lack of the gateway seems to prevent me from being able to RDP to the DA server for administration, is this another route issue?
Thanks for the awesome guide!
NEUR0
/ January 22, 2015Sorry a follow up to the above. I noticed the EXTERNAL NIC seems to now have an “autoconfigure” IP on top of my static IP which I configured based on the guide above. Why would it have this if DHCP is turned off? After deploying DA I got an error on the IP-HTTPS interface. Would it be due to this extra IP? Thank You Again!
Richard Hicks
/ January 24, 2015I apologize, but I’m not following you. If you could email me some screen shots I’d be happy to provide some feedback for you. 🙂
Richard Hicks
/ January 24, 2015The DirectAccess server will have access to the Internet via the external network interface, where the default gateway is assigned. Static routes are required for any remote internal subnets. The issue you describe (no access to RDP) sounds to me like you are trying to connect to the DirectAccess server from a remote subnet for which it doesn’t have a route to. If you resolve that issue I’m sure you’ll have RDP access. 🙂
Wayne
/ January 24, 2015I can vouch for this setup. If you’re going to use the DA server(s) in an edge scenario then the default gateway must belong to the internet facing adapter and the internal NIC cannot have one defined. Static routes must be defined for anything internal. This can be a lot of work, but thankfully it’s only a one-time deal. If you cannot RDP into the server from inside with this configuration make sure RDP is enabled and verify the static route is present to where you are trying to RDP from.
Craig
/ February 25, 2015If I want to use Teredo and I have two consecutive public IPs at my disposal I take it I just configure the external NIC with a second IP?
Richard Hicks
/ February 27, 2015Correct. Teredo will automatically be configured during DirectAccess installation if you have two consecutive public IPv4 addresses assigned to the external network interface. If you configure DirectAccess with only a single address and add another one after the fact, there’s an additional step you have to take. I’ll post that procedure soon.
Sohail Ahmed
/ April 12, 2015Hi Richard,
I got everything working except without specifying default gateway IP as DNS server, I cannot access internet. Can you please enlighten me on this?
Richard Hicks
/ April 14, 2015Not sure. If you have your routing configured correctly, everything should work. Double check that you can access all supporting infrastructure services (AD, DNS, PKI, etc.) from the DirectAccess server. If you can’t, you are probably missing a route.
Aljosa Agoli
/ October 23, 2015Hi Richard,
I have working da setup that is same as you wrote. I can access all server resources that are inside subnet 192.168.16.x resolving to their ipv6 addresses. From da server i can ping and remote to 128.1.0.x subnet and I have static route set on DA (on 192.168.16.87) to go there through 192.168.16.240 gateway. Problem is my Da clients cant connect to 128.1.0.x subnet. What am i missing? Is it possible to let clients also pass to this subnet.
Richard M. Hicks
/ October 24, 2015Not sure, but it sure does sound like a routing issue. DA clients should be able to access anything that is accessible from the DA server though. I’d suggest double-checking your routing configuration to ensure that traffic is getting back to the DA server correctly.
Aljosa Agoli
/ October 24, 2015Hello,
Thank you for your swift comment. It seems im not getting routes on my DA client, those I have on my DA server.
I am a bit confused as extra routes are not listed. It seems hop goes to my home router and then to Internet and not to DA server that probably should be gateway for these routes. I will have to recheck configuration unless im not understanding something crucial.
Richard M. Hicks
/ October 26, 2015Your client doesn’t need those routes. The client uses IPv6 exclusively to talk to the DirectAccess server. From there it is converted to IPv4 to get to the Intranet. The IPv4 routes only need to be in place on the DirectAccess server.
Mark
/ November 17, 2015The problem with this set up is that with Windows, leaving off a default gateway will cause the network location to change to ‘Public’, which will place your internal network connection under the public profile settings of Windows firewall, which can cause problems (such as lack of remote administration) as the Windows Firewall public profile is much more restrictive – and if you attempt to block everything outbound on the Public profile except for specific rules, that will casue you major headaches and a lot more administration.
Richard M. Hicks
/ November 18, 2015Hi Mark,
That shouldn’t be the case. If you’ve configured static routes correctly on the internal interface, the DirectAccess server should be able to reach a domain controller without issue and also enable the Domain firewall profile. If that isn’t happening, something else is probably wrong.
Jeff Singler
/ December 1, 2015I’m not following how the static routes work. Am I routing the internal nic subnet to the external nic gateway?
Richard M. Hicks
/ December 3, 2015No. The purpose of the static routes is to ensure that the DirectAccess server can reach any and all remote internal subnets. For example, let’s say your internal network is includes multiple subnets like 10.0.1.0/24, 10.0.2.0/24, etc. If the DirectAccess server is on the 10.0.1.0/24 network and has an IP address of 10.0.1.240, it could of course reach all hosts on that subnet without a gateway. However, to reach any other subnets internally it needs a route (because it lacks a default gateway – without a route it would be sent on the external interface, which isn’t where those networks are located!). The route to get to 10.0.2.0/24 would look something like this:
New-NetRoute -DestinationPrefix 10.0.2.0/24 -NextHop 10.0.1.254 (or whatever the gateway is for this subnet!) -InterfaceAlias “Internal”
Keep in mind you can summarize routes too. You could easily create a single static route for all of 10.0.0.0/8 if your entire internal network was in 10.0.0.0/8. Hopefully you get the picture. 🙂
Let me know if that helps!
Jeff Singler
/ December 3, 2015That clears it up for me, thank you. I was not sure if this was something I was missing or not. I have my DA working fine, clients are connected outside of corp network. But….I need manage out capabilities for a few different reasons, ccleaner network management and then RDP if I need it. I have Kaspersky as well and mostly that is pull, but sometimes it needs to push something out to clients. This is my main issue, I have followed a couple different guides for creating extra GPO’s for isatap and client FW extra rules. But it’s still not working.
Richard M. Hicks
/ December 3, 2015I’m happy to help. Drop me an email and we’ll talk in more detail. 🙂
Aljosa Agoli
/ December 3, 2015Hello, I just want to confirm that following this article, and replies Richard gave me I have concluded that the problem was in Cisco router. This lead to change of router to newer (fortigate) router after wich everything worked as written, I have tunnels connected through Direct Access to over 15 subnets and everything works as expected. I just have to add subnet on DA server, use local network gateway and (with a little help of DNS server) have Access to all Servers for management. Thank you Richard.
Courtney
/ January 28, 2016Richard – is this post valid for PPTP VPN setup with 2 NIC’s also? Thank you…
Richard M. Hicks
/ February 1, 2016Absolutely. 🙂
Carl Lucas
/ March 16, 2016I have two NIC’s installed in the 2012 DA. I would like to have the VPN access be able to access the internet without the need of a proxy server. Is that possible?
Richard M. Hicks
/ March 16, 2016Over VPN? Yes. Over DirectAccess, assuming you have force tunneling enabled, I’m not sure. I’ve only ever configured force tunneling with on-premises proxy servers.
Wayne
/ March 17, 2016Yes, this is possible. The RRAS routing configuration will be the trickiest part.
Richard M. Hicks
/ March 18, 2016The experience isn’t likely to be without issue. If web pages load content using an IPv4 address as opposed to an FQDN, it will fail to connect over DirectAccess. Hopefully that doesn’t happen too often though.
wafaa
/ June 7, 2016Excellent blog .
I have 2 subnet and 3 network interfaces .
first subnet 192.168.0.0/24 and the second 192.168.10.0/24
how configure my windows server 2012 r2 as router with one dns and dhcp for there 2 subnets
Thank you
Richard M. Hicks
/ June 11, 2016The guidance in this post is pretty clear. Just create the static routes to your remote internal subnets using your network’s default gateway as the next hop. 🙂
David Straede
/ September 9, 2016We have a native IPv6 Intranet and IPv6 Internet that tests perfectly, a whatismyip.com and a ping to google.com show IPv6 traffic only. There seems to be little documentation how to configure the NIC cards and DA in this rare setup. Can you point me to any docs on this? Thanks!
Richard M. Hicks
/ September 12, 2016There is very little (if any) documentation for this deployment scenario. I did touch upon this topic in my upcoming book though – http://directaccessbook.com/. Ultimately it isn’t difficult to implement. If you have native IPv6 addressing you would assign those addresses to the DirectAccess server’s network interfaces accordingly. The real challenge is ensuring that traffic is routed back to connected DirectAccess clients correctly. If the DirectAccess client is using a transition technology, no problem. The prefixes for DirectAccess clients are unique and can be routed back to the DirectAccess server without much hassle. The real challenge is when your DirectAccess clients have a native IPv6 address. This typically results in asymmetric routing, where traffic from the DirectAccess client comes in through the DirectAccess server, but attempts to egress through the internal network’s default gateway. Commonly, a stateful firewall is inline and prevents this return traffic. There’s no good way to route this traffic back to the DirectAccess server because the client has a unique public IPv6 address (GUA). In this scearnio, it is recommended that the DirectAccess server be deployed in a perimeter network behind the internal network’s border router/edge firewall. In some cases it might even be easier not to put a public IPv6 address on the DirectAccess server to ensure that all DirectAccess client traffic uses a transition technology. This will greatly simplify IPv6 routing and eliminate potential asymmetric routing issues.
David Straede
/ September 14, 2016That seemed to do the trick, I set public NIC to automatic IPv6 so it only has the local link address, and put in on the DMZ with only IPv4 443 open to it. I left the static IPv6 on the internal NIC, but no IPv6 default gateway. Since all our clients are Windows 10, seems like IPHTTPS is the way to go.
C Osborne
/ October 17, 2016Hi Richard,
I have found your site very informative and useful. However I have an issue with regards to our Direct Access clients not being able to resolve the directaccess-webprobehost address (NCA). I thought this was a DNS issue so I created a Host A record for that address to the ip of our DA server but this made no difference. I have checked multiple internet website addresses and I do an nslookup from the DA server they all fail.
I was looking through this page and saw this: “One last change that needs to be made, and perhaps the most critical and often overlooked setting, is the network interface binding order.”
I checked this on our server and the binding order is indeed wrong (DMZ above LAN), but all the clients are working. That said I am seeing some odd errors so In an effort to make sure everything is configured correctly I am checking the whole setup. To that end my question is, if the binding order was wrong (as ours is) do you know what errors I could expect to see? I ask this specifically as you have said this is critical.
Thanks.
Richard M. Hicks
/ October 19, 2016The only time I’ve ever seen incorrect network interface binding order cause an issues is when there are DNS servers configured on the external interface. DNS servers should only be configured on the internal network interface. If that’s the case for you, I’d say that this isn’t the issue. However, it is a good idea to fix it. You should be able to resolve the web probe host name to an IPv4 address on the DirectAccess server. If you can do that, verify the same on a DirectAccess client. Remember that nslookup won’t work unless you specify the DNS64 address. I recommend using the Resolve-DNSName PowerShell command as it works with the NRPT on the DirectAccess client.
Kevin Boucher
/ October 22, 2016I have used these settings for a small test server using Windows 2012. My server is also my domain controller and I am running into tons of trouble with NLA placing my external NIC in the domain. I cannot run the configuration wizard for remote access as it says it can’t find a network adapter w IPv4 with external address and no domain profile. Any ideas on how I can overcome this? There are a few things posted on the Internet about blocking the card from seeing the domain controller which I have tried. Unless I’m doing that incorrectly I’m at a loss.
Richard M. Hicks
/ October 24, 2016This is one of the reasons that installing the DirectAccess role on a domain controller is not recommended. That’s not to say it isn’t possible though. 😉 However, I have no experience with this configuration and don’t have anything useful in the way of guidance to offer you. :/
Alper Ozbek
/ September 22, 2022Hello Kevin,
I am stuck at the same situation. I could not figure out a way to remove my external nic from domain network and making it public. Did you make a progress on the matter? I have only one server running domain controller on, and I also must use that for direct access. Any help is very appreciated. I looking for a solution almost a week.
Richard M. Hicks
/ September 23, 2022Installing DirectAccess on a domain controller is definitely not recommended. I’d suggest placing that workload on a separate server.
Jan Nielsen
/ January 17, 2017Thanks for a good guide.
Is it possible to do the changes to the NICS after you have installed DirectAccess without messing up the DirectAccess setup ?
/Jan-
Richard M. Hicks
/ January 18, 2017No. Changing the NICs after DirectAccess is installed will result in a broken configuration. However, it is sometimes possible to simply select the new NICs in the Remote Access Management console again and everything will work. In my experience though that doesn’t always work. :/ DirectAccess is tightly couple with the network interfaces and even changing IP addresses can break DirectAccess.
lukaszc
/ January 29, 2017Hi Richard,
Before our DirectAccess deployment I read your book. It’s great and helps a lot.
However I’m confused what routes should be added and where.
Internally we have mixed deployment of IPv4/IPv6 where each host has both addresses set as static. I can establish DirectAccess connection from an external client but I cannot access any internal resource until I add on this resource IPv6 interface an IPv6 internal address of my DirectAccess server as a gateway. Than I can access it but only with IPv6 address, IPv4 doesn’t work.
May you elaborate what’s the best practice in such situation?
BR,
Lukasz
Richard M. Hicks
/ January 30, 2017There are a number of issues and challenges associated with deploying DirectAccess with native IPv6. If you have IPv6 deployed internally, that’s usually fine. However, if your DirectAccess server has an IPv6 address on its external network interface and clients can connect without using an IPv6 transition technology, then it can be problematic. The only workaround I’m aware of currently is to configure the DirectAccess server as your internal network’s default gateway. If you can’t do that (and probably shouldn’t anyway) then it is suggested that you ensure the DirectAccess server is reachable from the public Internet via IPv4 only. After that, as long as the DirectAccess server has routes to any remote internal networks (IPv4 or IPv6) it should work.
Warren Brown
/ February 3, 2017Just starting to build our test environment. Your site was so good, that we ordered your book.
Server 2016 doesn’t seem to have the options to configure the NIC adapter order. I do not have a “Adapters and Bindings” tab shown at all. Apparently no components use the binding order any longer (https://blogs.technet.microsoft.com/networking/2015/08/14/adjusting-the-network-protocol-bindings-in-windows-10/). The new method of controlling flow is to set the route metrics, such as with Set-NetIPInterface –InterfaceIndex “xx”–InterfaceMetric “xxx”. Does this match up with your experience and understanding?
Thanks for the great site, and really appreciate your great book on the topic.
Richard M. Hicks
/ February 4, 2017Thanks for purchasing the book! If you would be so kind as to review it on Amazon.com I’d appreciate that tremendously. 🙂 When I was writing the book I was using Windows Server 2016 Technical Preview 4 (TP4). There was a bug in TP5 that prevented DirectAccess from working correctly, so I was stuck using TP4 for the duration of the book. When Windows Server 2016 was finally released, I did notice that they removed the option to change the network interface binding order (might have been removed in TP5, but I didn’t spend much time with that release). According to Microsoft, there is no longer any need to make this change, so I’m good with that. The real reason network interface binding order was even an issue previously had more to do with name resolution, but that’s no longer an issue now. I’ve not encountered any scenario in which I’ve had to make route metric changes. With that, I’d say that configuring network interfaces as outlined in the book will yield acceptable results. No need to make any other changes as far as I’m concerned.
Hope that helps!
Mukesh Kumar
/ June 11, 2017Hello Richard…
Very well way to esay understand but please can u explain the IP scnerio with topology..
Richard M. Hicks
/ June 11, 2017The IP addressing I used is just an example. You can use whatever IP addressing you desire, really. The important thing is that the internal and external interfaces have to be on different subnets, that’s all. 🙂
Reggie
/ June 15, 2017Hi Richard,
PLEASE HEEELP!!
I am a total Newbie and my host is Windows 10 with Hyper V activated. I have only one NIC and I would like to set up a lab where I have a VM Domain Controller using it’s own ADDS, DNS and DHCP that includes window 10 and 7 clients, However this VM LAN should exist on a seperate IP subnet from my physical router. However it should be able to access the internet.
I would then like to add another 2012 R2 Server with windows 10 and 7 clients on yet another IP subnet /VM LAN2) with the ability to talk back and forth with VM LAN1. It should also have internet access.
Is this set up the right one for me? How should I set this up. I am desperate and need help.
Thanks!!
Richard M. Hicks
/ June 19, 2017I’d suggest having a look at Microsoft’s test lab guides. Here’s a link to the base configuration guide which provides instruction for setting up a basic lab environment. If you have the resources, you should be able to do this on your Windows 10 client machine – https://www.microsoft.com/en-us/download/details.aspx?id=6815. Also, there are some specific test lab guides for DirectAccess here – https://technet.microsoft.com/en-us/library/mt652202.aspx.
zubair
/ August 22, 2017Sir on an external interface do we have to define our public ip or not ?
as you configured private ip address on both internal and external interfaces.
kindly guide me that how we will configure our public ip and what will be then DNS and default gateways ?
waiting for your response.
Richard M. Hicks
/ August 22, 2017You do not have to assign public IP addresses to the external interface of your DirectAccess server. In fact, that is not recommended. It is recommended that you use private IP addresses and NAT the traffic from your public IP address on your edge firewall. How that is done will depend on the model of firewall you have. DNS servers are configured only on the internal interface and they are your corporate AD DNS servers. No DNS servers should be configured on the external interface. The default gateway is configured only on the external interface and it will be your firewall’s IP address.
ZUBAIR
/ October 15, 2018thank you sir…
my server DNS is on first NIC = 192.168.10.2
my default gateway is = 192.168.10.1.
i want to configure second NIC card for vpn..i dont know the that what will be ip scheme for that…what will be default gateway and what will be dns. kindly solve my problem. thank you again.
Richard M. Hicks
/ October 20, 2018You’ll remove the gateway from the internal NIC and add it to the external NIC. The gateway will depend on your networking configuration. DNS will stay on the internal NIC.
Ulrik
/ September 14, 2017Followed your guide for this 2 nice setup, and want to also use RRAS SSTP VPN on the DA server. The VPN client on Windows 10 can connect and authenticate, but no traffic flows through the tunnel (ping SMB etc). Any tip to what the culprint is?
Richard M. Hicks
/ September 16, 2017Could be any number of things, but most commonly it is a routing issue. Make sure the remote access server has access to whatever you want your clients to connect to. If it does, it should work for the client as well.
Ahmed K
/ December 9, 2017I have set up FTP server running Windows Server 2012 R2. I have two NIC cards, one I have assigned a Public IP address – 41.223.59.153/30. this one is accessible from the internet.(remote users log in with this) the 2nd is private – 172.18.20.188/24 ( this one is only accessible from the LAN users).
problem comes because I have two default gateways. when they are both up, I cannot reach the server via the LAN .But I can reach the server via the Internet. when I disable the Public IP address, I can only access via the LAN.
what is the best practice solution for this problem ??
thanks in advance
Richard M. Hicks
/ December 11, 2017As I outlined in this post, a multihomed Windows server can have only one default gateway. Most commonly the default gateway is configured on the external-facing interface. The internal interface must not have a default gateway defined. This will make your FTP server reachable from the Internet, and clients will have access to anything on the subnet where your server has a network interface. The FTP server would also be reachable from your internal subnet as well. However, if you need to access your FTP server from a different internal subnet, you’ll need to create a static route on the internal interface. You can follow the guidance outlined above to accomplish that. Have fun!
bestboho
/ January 23, 2018Problem with a multi-homed setup. DMZ and Internal NIC’s in place. Default gateway through the external facing DMZ interface. Routes to internal networks were added manually. Everything works fine expect if I want a public website to go through the DA tunnel (adding it to the nrpt table) is does not work. From the DA server it is reachable and goes through the external interface. If I manually route the website ip address through the internal NIC, it works fine. However, I would like to route the public facing website through the DA servers external NIC.
What am I missing?
The reason why I want a public website to go through the DA server is because some websites uses our corpnet’s public IP address to identify and grant explicit access.
Richard M. Hicks
/ January 27, 2018You’ll need to define a proxy server for this to work. Details here.
bestboho
/ January 28, 2018Okay, in MS documents I think they state that you can use a proxy. Did not think it was mandatory…
Wayne
/ January 27, 2018Then you’ll need to specify the external sites in the NRPT GPO. This will force the clients to use DA as their gateway. Then the internal networking will kick in and send them out the corporate firewall, achieving your desired result.
bestboho
/ January 28, 2018@Wayne, this is exactly what I’ve done and it does not work. Only way is to route the external website ip addresses through the internal NIC. But that is not the desired solution.
Wojciech
/ March 30, 2018Hi Richard,
Big kudos to you for all your work on Direct Access. I’ve been following your blog and your videos on Pluralsight for a while now, getting myself ready to deploy a DA setup.
I’d be really grateful if you could answer a few questions:
1) What are the advantages of using a double-NIC setup over a single-NIC one? In my case the external NIC would be in a DMZ. The dual-NIC setup seems more complex and I’m wondering if it’s worth the effort.
2) Are there any differences between a single-NIC and dual-NIC setups when NLB is concerned?
3) Could I just set up a static default route (0.0.0.0) to point to my internal network? Or do I have to do a separate entry for each internal subnet?
Kind regards,
Wojciech
Richard M. Hicks
/ April 2, 2018Thanks for the kind words. Much appreciated! 🙂
The advantages of using two NICs is security. With two NICs configured you can enforce a much more strict Windows firewall policy on the external network interface, which reduces the exposure of the DirectAccess server to untrusted networks. Using NLB with one or two NICs is fundamentally the same. Finally, you will need to create individual static routes to internal subnets. You can’t create a 0.0.0.0/0 on the internal interface because that would essentially be another default route, which will break things. 🙂
Wojciech
/ April 3, 2018Hi Richard,
Thanks for the info. I want to make sure if I understand everything correctly:
1) With a single-NIC setup, not only would I have to open the necessary ports to and from the DMZ from the outside, but also from the DMZ to all the internal resources I want to access.
2) With a Dual NIC setup, I can limit the firewall to allow only the necessary ports to and from the DMZ on the outside interface, and the internal communication is handled by whatever FW rules are applied to the network the “internal” interface is connected to.
Am I on the right page?
Kind regards,
Wojciech
Richard M. Hicks
/ April 3, 2018That’s correct. The single-NIC in a DMZ deployment is not recommended. Not only is it more difficult to configure, it presents a significant security risk too. As the DirectAccess server needs access to all internal domain controllers, an attacker who gains a foothold in the DMZ could easily spoof the DirectAccess server’s IP address and would then have access to sensitive internal resources. It is much better to have two network interfaces, one in the DMZ and one in the LAN. The DMZ interface only listens on TCP port 443 and has no access to the internal network.
Wojciech
/ April 13, 2018Hello Richard,
One more question about the dual-NIC and NLB setup. I understand that for Direct Access to report everything working, it needs to be able to connect via HTTPS and ICMP to the NLS server. Is it enough that the NICs on the internal network have connectivity to the NLS, or do I need to open up that traffic from the cluster address (which will be in the DMZ) to the NLS server?
Kind regards,
Wojciech
Richard M. Hicks
/ April 14, 2018You should only have to allow access from the dedicated IP addresses of the internal interfaces of each DirectAccess server. No traffic will originate from the NLB VIP.
Wojciech
/ April 16, 2018Brilliant. Thank you!
Kind regards,
Wojciech
Erwin En Isis
/ January 21, 2019Hi Richard, we are currently running a single nic Win 2012 R2 DA server and would like to change the config to multi homed exactly like the config in this article. Can we just add an extra nic to our server, add the settings as described in this article and run the wizard again or do we need to install a new server and perform a migration?
Kind regards,
Erwin
Richard M. Hicks
/ January 21, 2019I’m not sure about that. It’s not something I’ve ever tried, so I don’t have any experience to share with you unfortunately. You can certainly try, but it might not work. Make sure you have good backups (server and GPOs!) or be prepare to rebuild if it goes sideways. 🙂 Let me know how it goes if you decide to try it!
Erwin En Isis
/ January 22, 2019We decided to go with a more safe solution because our clients are all over the country and we can’t take the risk of have a lot of clients with connection issue because they need a policy update for which they need to be in the office.
We are going to install a new separated multi homed DA server as a second entry point and will not connect this one to the primary so we can migrate our clients manually when they are in the office 😉
Richard M. Hicks
/ January 22, 2019Probably a good idea. 🙂
SysAdmin
/ January 27, 2019Excellent post. However, it did not work for me. In my virtual lab, I have PFSense as the firewall and router with 3 NIC: WAN (Bridge to my desktop host NIC), LAN (10.1.0.0/24) and DMZ (172.16.0.0/24). I have 2 DC in a forest 10.1.0.0 / 24 (LAN) and DirectAccess Server with 2 NICS: LAN & DMZ. In DirectAccess Server, before joining the domain, the 2 NICs are clearly seperate. However, after joining to the domain, the External NIC is given a domain profile. If I disable the LAN, then the External NIC does not get a domain profile. Re-enabling LAN, the External gets a domain profile. I’ve checked all the settings you pointed out there and the solution still does not work.
Suggestions?
SysAdmin
/ January 27, 2019Nevermind. Found out the problem. Have to actually enable all the Windows Firewall for the rules to work after rebooting the server.
Richard M. Hicks
/ January 28, 2019🙂
Kurdistan
/ July 30, 2019Thank you Richard for your article its very useful. even though its 4 years old
Richard M. Hicks
/ August 1, 2019My pleasure! FYI, some of this no longer applies in Windows Server 2016 and later. For example, you can no longer configure interface binding order in the UI. The IP address and routing configuration is still relevant though. 🙂
Kurdistan
/ August 1, 2019That’s correct. Less hassle
ALON373
/ December 29, 2019First i want to thank you Richard, i try this and i don’t sure if it is work correctly. i successfully connected to the vpn server and got an IP address bout fail to ping from PC that connect to my LAN to one of my vpn client. can you help me?
Richard M. Hicks
/ January 2, 2020To start, make sure you can ping any resources you want to reach from a client from the VPN server itself. If you can do that, the client should be able to as well. The client will never be able to reach anything the server can’t (at least from a routing perspective). Another common configuration issue is routing. If you are using using a unique IPv4 subnet for your VPN clients, your internal network routes must be configured to return that traffic to the VPN server. If this is missing, client traffic may reach an internal server, but the return traffic never makes it back.
Carol Ostos
/ May 23, 2020For dual homed interfaces, does it matter if the external facing (DMZ) interface is configured with either network category “Public network” or “Private network”? If yes, what is the recommeded network category. Thank you in advance for your help!
Richard M. Hicks
/ May 25, 2020Either is fine. I typically treat them as the same and create firewall rules that apply to both.
Carol Ostos
/ May 25, 2020Thank you Richard. I had a closer look at the profiles and both were similar so for consistency I changed it to Private using the Set-NetConnectionProfile.
Reference: https://www.jorgebernhardt.com/how-to-force-a-network-profile-in-windows-using-powershell/
Validated service availability and all looked good.
Once again, appreciate the time.
Carol Ostos
/ May 26, 2020Hi Richard, if I may, are we able to install AV software (with of course relevant exclusions) on the DA servers. Our NLS servers have it but we dont have it on the DA servers. Just trying to double check as I could not find anything in the actual MS documentation aside the recommendation to avoid installing DA from an imaged OS precanned with customised third party software because that could cause issues. If we are able to install AV that would make us happy so hoping you can point me in the right direction? Much appreciated again!
Richard M. Hicks
/ May 27, 2020Installing antivirus/antimalware on the DirectAccess server isn’t generally recommended, but it should be supported. You’ll want to exclude the C:\Windows\DirectAccess\Db folder from file scanning and also make sure that there are no restrictions for IPv6. Should work though. 🙂
Kola Lawal
/ June 25, 2020I have two mikrotik router, one for the isp configuration and the other for my local area network linking up to the previous(ISP mikrotik router) and a windows server 2012. i have try to configure the vpn for the server and i couldn’t connect due to what i couldn’t figure out but i want to know if i need to do some work on the wan or local router to enable my vpn connection or if i should follow the above procedure without working on the router
Richard M. Hicks
/ June 29, 2020I’d expect it to work as long as there was connectivity and the routes were all in place correctly.
Matthew Ikechukwu
/ December 28, 2020Hello
I am really curious about the VPN thing. I have a client we have developed a desktop application and the client have two branches, however, in all they are not up to 25 Employees, and we want to take advantage of VPN logon. We have setup windows 2012 Standard with 2 Net Cards. A Wireless Router for Lan connection in Domain Network and public Internet.
Here is our intention correct me if I am wrong
Lan Internal: Card1 IP 192.168.0.2
Wireless Router IP 192.168.0.1 – Static
Domain: CompanyName.Local (the company has domain name used in hosting website with another company)
DNS: IP 192.168.0.2 -The server IP
External Card: The same with Provider IP address or If permitted Open a Local port with same ISP IP range
The application runs on SQL 2012 Database
Firewall: allow Domain
Can these IP configurations allow users from the other branch logon into the server from any internet access on their computer after VPN Configuration on a server? Of course, all the employee computers must join Domain and VPN Configured before delivering to the Employee.
Please, your respond is highly appreciated
Engr. Matthew Ikechukwu
Makai Info Tech
https://www.makaiit.com
Richard M. Hicks
/ December 28, 2020Assuming all of the routing is in place I would expect this to work.